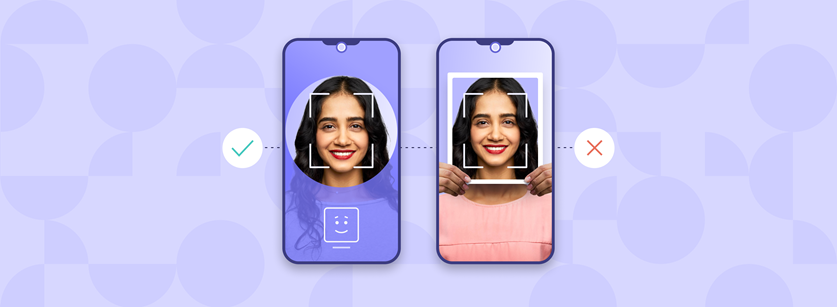
What are the advantages and disadvantages of biometrics?
In our vast, interconnected and increasingly digital world, the need to prove who we are from a distance has become routine. As citizens and consumers, we are often called on to provide evidence of identity online. Where extended due diligence is essential and when the risks associated with a transaction are high, document-centric methods of identity verification are often preferred and identity authentication techniques have become of paramount importance to the identity proofing processes.
Our biometric data, our face, fingerprints, eyes (iris and retina) and voice, has become an everyday method of authenticating who we are.
What is biometric authentication?
The different types of biometric authentication offer a secure process of proving we are who we claim to be by using our unique physical or behavioural characteristics. Biometric authentication is commonly used in device security, financial transactions, immigration controls and patient identification in private healthcare among many other applications.
All biometric recognition systems rely on the comparison of a digital representation of a physical or behavioural feature with a previously recorded template. It’s essentially pattern recognition that matches individuals by their biometric traits.
Biometric systems should operate to a specified recognition accuracy, meet speed and organizational resource requirements, be accepted by and harmless to the people using them and be sufficiently secure to resist fraudulent attacks on the system.
Onboard good customers in seconds with FaceMatch facial recognition software.
So, what are some of the advantages of biometric authentication?
Biometric authentication is fast and convenient
While some forms of biometric authentication are faster than others, most processes can be completed in matter of seconds, providing a convenient and secure digital defence against identity fraud. And with no PINs, passwords or other knowledge-based responses required, biometrics don’t tax our memories in order to deter imposters. The real convenience of biometric authentication solutions is that we carry our credentials with us wherever we go.
Biometrics offer a high level of security
Unlike knowledge-based systems, biometric authentication systems do not present a target-rich environment for hackers. Mass cyberattacks and large-scale data breaches do not present the same threat to our biometric data, which almost requires individual targeting to stand any chance of success.
The impersonation of an individual’s physical characteristics (often referred to as a ‘presentation attack’ or ‘spoof’) requires sophisticated circumvention of scanner or camera sensors in a biometric system which can be rendered still harder with liveness checks for genuine presence.
Liveness checks
Liveness detection ensures that the person submitting biometric data is real and genuinely present at the time the data is detected and captured. In face recognition, for example, this prevents the use of any impersonation tool such as photographic printouts, deep fake videos and silicone masks when submitting facial images.
Genuine presence is hard to fake
Confidence in online biometric authentication is directly related to the genuine presence of the owner of that identity when it is presented – in the same way that robust immigration processes require that we present our own passport to border control.
Liveness detection technology is evaluated and graded by the US National Institute of Standards in Technology to ensure the highest standards are achieved. By coupling biometric identity authentication with liveness or presentation attack detection, biometric systems are hard to spoof. In facial recognition, for example, a still photo of a face or a rubber mask will fail the genuine presence test.
What makes a great biometric identifier?
Our face, fingerprints and eyes have all become everyday methods of proving who we are. But what are the features of a biometric trait that make it useful for authentication?
Universal
Every individual accessing the system should possess the same feature.
Distinctive
Biometric characteristics should be sufficiently different to distinguish any two individuals.
Permanent
The biometric identifier should not change significantly with time or with age.
Measurable
The digitized feature should provide recognition speed and accuracy.
So, what are the drawbacks to biometric methods of identity authentication?
False biometric matches can occur
A false match can occur when the biometric data of two different individuals is confused. Although rare, this can happen in the case of twins or similar-looking siblings, if the biometric reader is improperly calibrated or malfunctioning, or if the database used for comparison has incorrectly recorded an individual’s biometric template.
To successfully reduce the false acceptance rate (FAR) in biometric authentication systems, the system must be able to capture high-quality biometric samples and regularly update biometric reference templates to correctly match against enquiries.
Rejecting legitimate identities
The reverse error can also occur when a known identity is falsely rejected by a biometric authentication system. This can happen when a person’s biometric traits change; for example, if an older person’s fingerprint has become worn with age, or, in the case of facial recognition, due to a change in appearance prompted by weight loss or weight gain. Poor image capture quality caused by blur or glare can also result in false rejection.
Again, ensuring that the sensors that systems rely on capture high-quality biometric samples and templates are regularly updated will minimise the false rejection rate (FRR).
Build trust and beat fraud with secure identity document verification.

Determining a match of biometric identifiers involves complex pattern recognition and decision-making processes within an authentication system. FAR and FRR can be controlled by configuring the system for maximum security or minimum friction, and very often a sweet spot between the two that’s suited to the use case.
Care must be taken to avoid biometric bias
Biometric authentication systems are powered by machine learning algorithms. In past studies, The US National Institute of Standards and Technology revealed that African-American and Asian people experienced a 10 to 100 times higher FAR compared to Caucasian people when encountering some facial recognition systems.
Care must be taken to train these algorithms on data sets that are inclusive and do not inadvertently discriminate against any demographic or result in racial bias. To avoid unintentional partiality, the best authentication systems follow ISO standards to ensure the design and development of AI systems and applications that do not discriminate or disadvantage any group, or deny access to essential digital services.
Secure and smooth digital experiences
Speed and convenience matter as much as security for successful brands looking to build customer relationships based on trust. A great digital experience and a safe experience matter to both businesses and consumers. So, identity verification systems need to balance these and adjust for greater security or greater convenience according to the context and the needs of the organisation or business.
Multimodal biometrics systems can combine authentication checks against several biometric features, such as, the face and the iris, or the iris and fingerprints. These systems can overcome some of the disadvantages of unimodal systems and help to increase security and accuracy at the expense of speed.
Alternatively, by layering identity data verification checks, such as name, date of birth, and address alongside biometric authentication, it’s possible to quickly triangulate trust in that person’s identity with reference to credit bureaus or mobile operator databases, fast tracking confidence in history of that digital identity.
Frequently Asked Questions
How reliable is biometric authentication?
Biometric authentication is highly effective, but not infallible. For example, fingerprint scanners can be tricked by using a fingerprint impression, facial recognition systems can be fooled by silicone masks and iris scanners can have trouble detecting certain eye colours or may not work well if you wear glasses or contacts.
Is biometric authentication biased?
Biometric authentication technology is not biased, but as with all AI and ML solutions, biometric algorithms benefit from and respond to training with varied and inclusive data sets. The latest datasets have reduced demographic bias, making biometric processes more globally inclusive and effective than first-generation solutions.
Can smartphones be used for biometric authentication?
Biometric authentication technology has long been built into mobile devices and has become more widely available and affordable over time. Most smartphones have fingerprint scanners built into the home button and voice recognition is regularly used as an input to various smartphone apps.
Can I combine data checks with biometric authentication?
Yes, this is good practice. An identity is made up of several different elements. By layering data checks, such as name, date of birth, and address, with documents, devices and biometrics, your business can build a better picture of your customer's identity and you can provide a better onboarding experience.
How much does biometric authentication cost?
Biometric authentication is a more expensive solution than a simple password or PIN-protected system. As identity-proofing technology powered by biometric authentication has advanced, however, it has achieved a price point comparable with alternative identity verification solutions.
Sign up for more expert insight
Hear from us when we launch new research, guides and reports.