Risk-based journey builder
A risk-based approach lets you focus on optimal customer experiences and improved cost-per-customer acquisition.
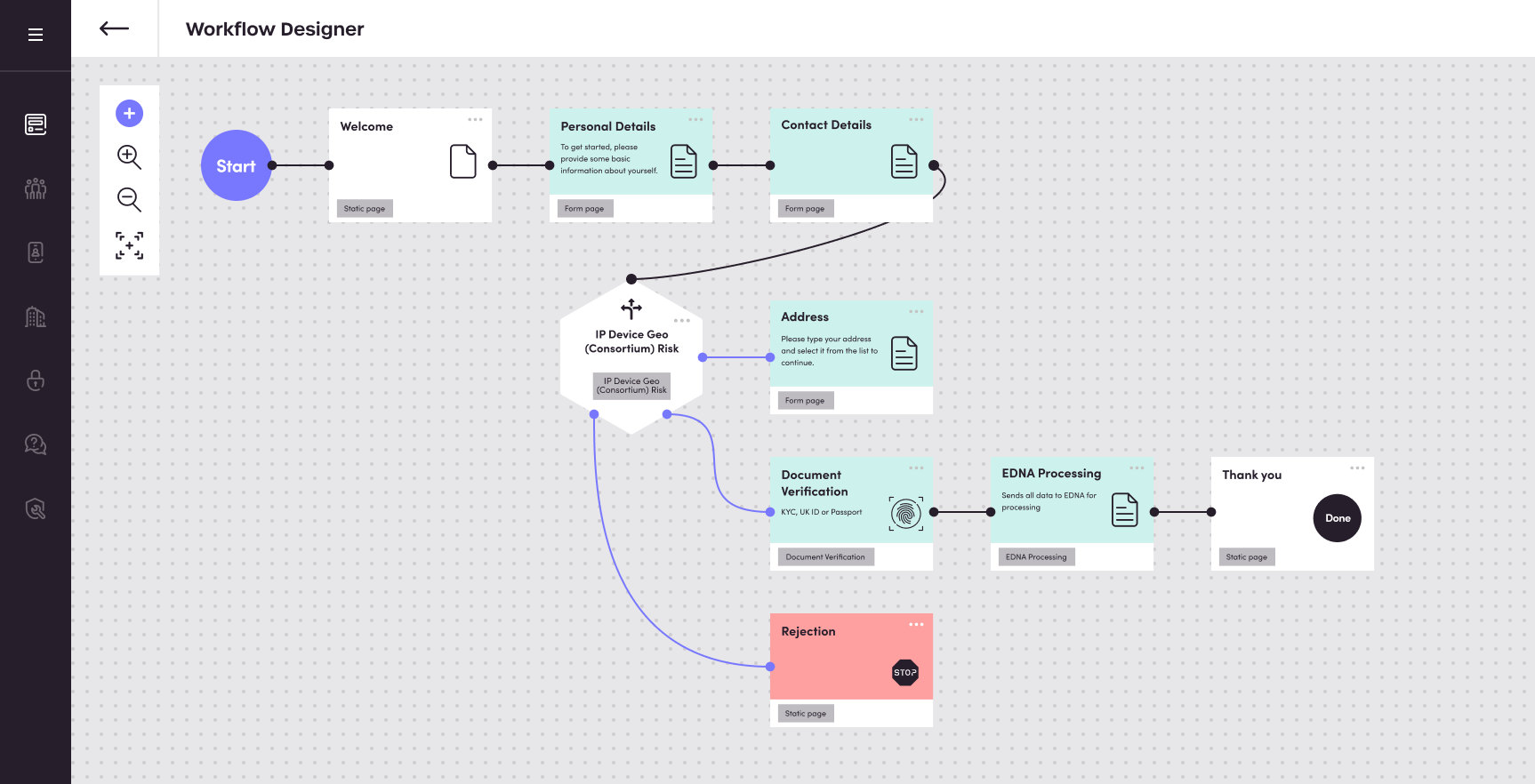
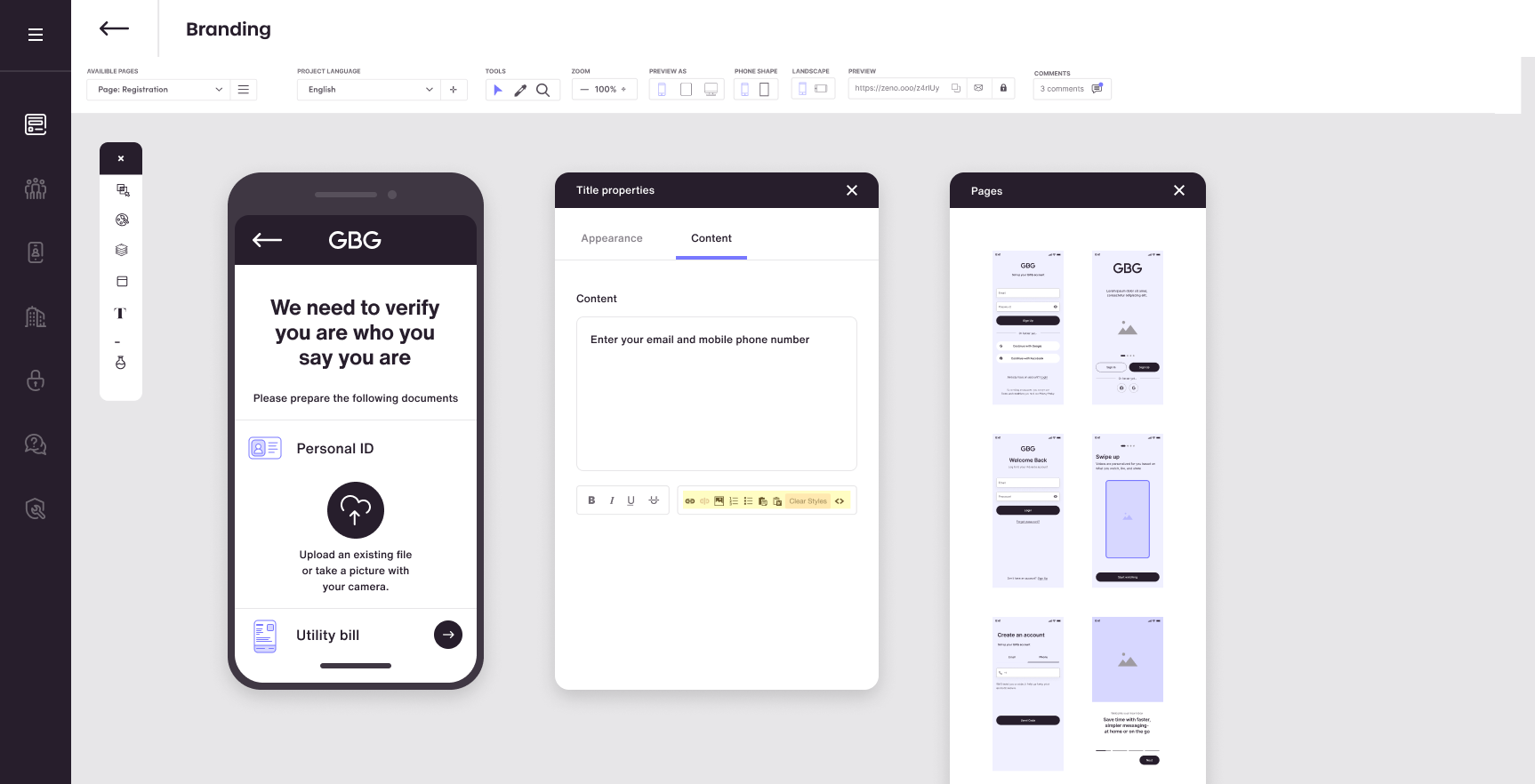
UI Editor
Easily convert trusted customers fast. With no-code customer journey builder, templates and built-in branding get to market in minutes - not days.
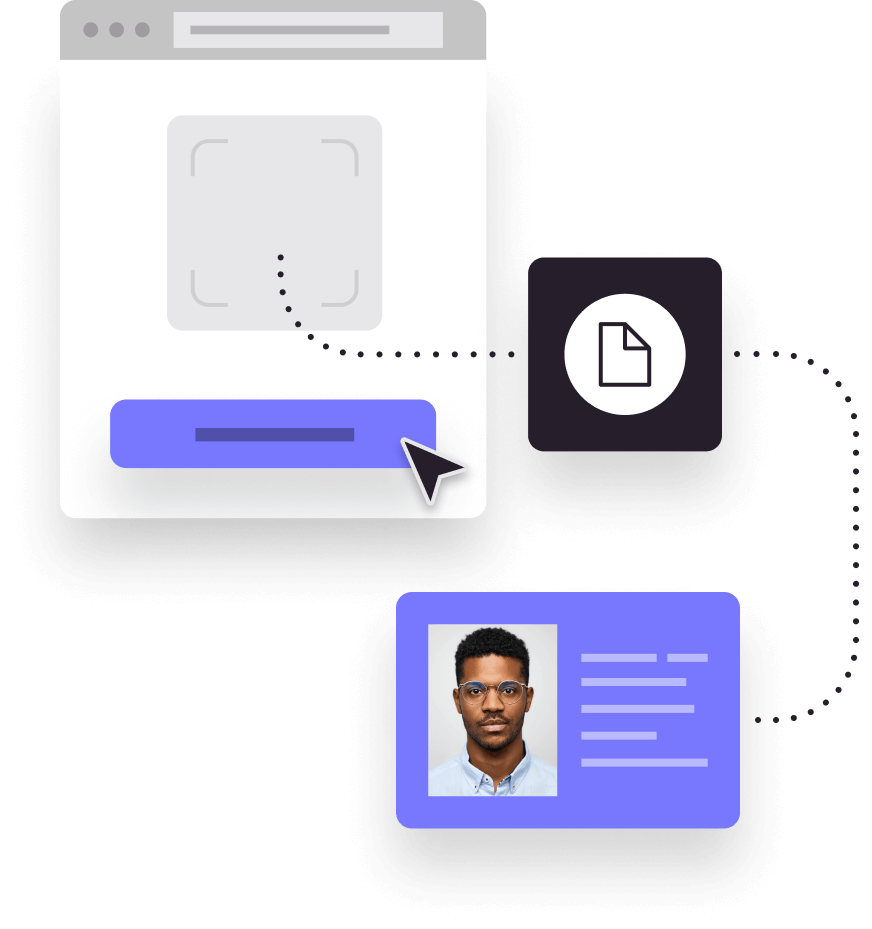
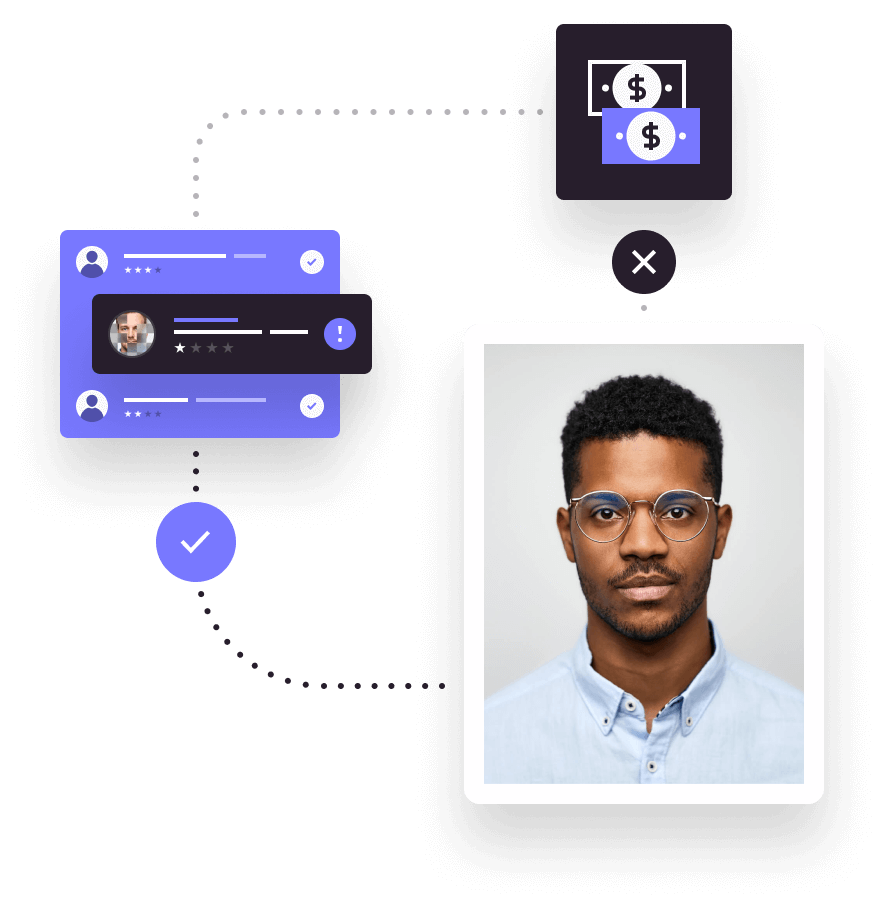
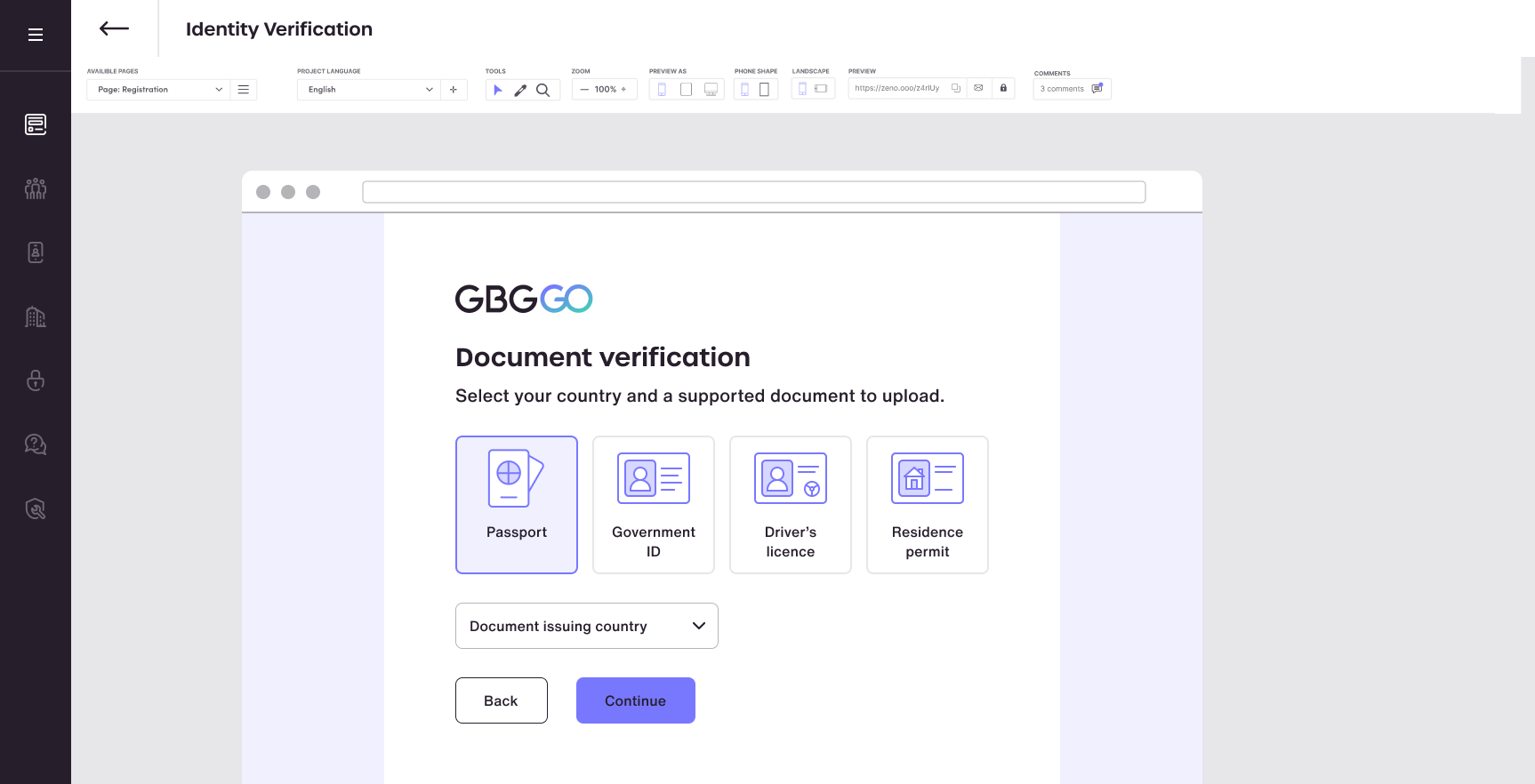
Identity & document verification
Secure document-centric and biometric verification with AI-powered decisioning combine to minimise risk, fast-tracking only trusted customers.
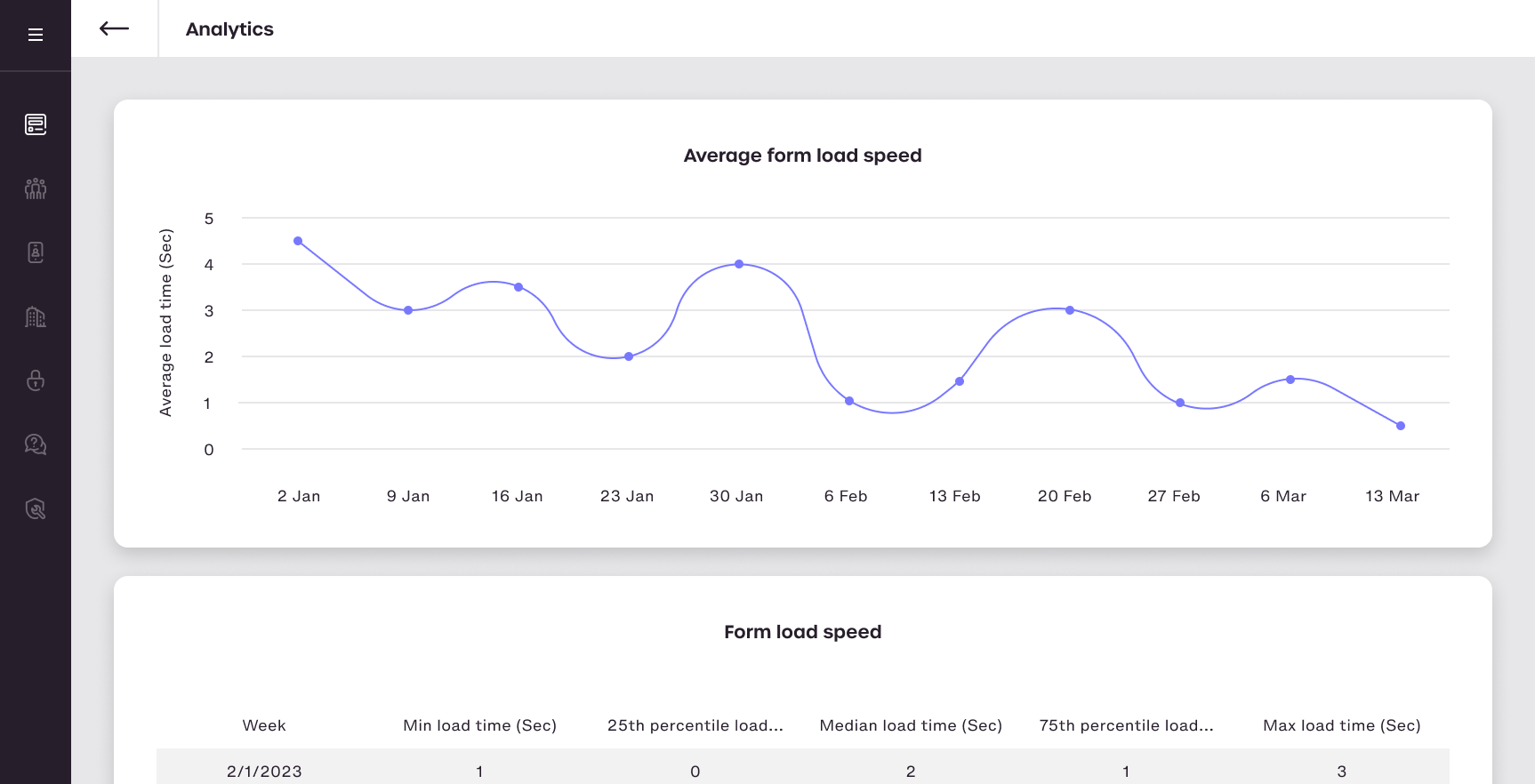
Analytics
With real-time analytics of journey times, screen performance and drop-off locations, optimise customer journeys for higher onboarding rates and revenue.